Following the publication of Dev Joshi‘s brief on I&IC documentary blog yesterday, I took today the opportunity to briefly introduce it to the interaction design students that will be involved in the workshop next week. Especially, I focused on some points of the brief that were important but possibly quite new concepts for them. I also extended some implicit ideas with images that could obviously bring ideas about devices to build to access some past data, or “shadows” as Dev’s names them.
What comes out in a very interesting way for our research in Dev’s brief is the idea that the data footprints each of us leaves online on a daily basis (while using all type of digital services) could be considered as past entities of ourselves, or trapped, forgotten, hidden, … (online) fragments of our personalities… waiting to be contacted again.
How many different versions of you are there in the cloud? If they could speak, what would they say?
Yet, interestingly, if the term “digital footprint” is generally used in English to depict this situation (the data traces each of us leaves behind), we rather use in French the term “ombre numérique” (literally “digital shadow”). That’s why we’ve decided with Dev that it was preferable to use this term as the title for the workshop (The Everlasting Shadows): it is somehow a more vivid expression that could bring quite direct ideas when it comes to think about designing “devices” to “contact” these “digital entities” or make them visible again in some ways.


Philippe Ramette, “L’ombre de celui que j’étais / Shadow of my former self “, 2007. Light installation, mixed media.
By extension, we could also start to speak about “digital ghosts” as this expression is also commonly used (not to mention the “corps sans organes” of G. Deleuze/F. Gattari and previously A. Artaud). Many “ghosts”/facets of ourselves? All trapped online in the form of zombie data?
Your digital ghosts are trapped on islands around the cloud – is there a way to rescue them? Maybe they just need a shelter to live in now that you have moved on?
… or a haunted house?
And this again is a revealing parallel, because it opens the whole conceptual idea to beliefs… (about ghosts? about personal traces and shadows? about clouds? and finally, about technology? …)
What about then to work with inspirations that would come from the spiritualism domain, its rich iconography and produce “devices” to communicate with your dead past data entities?

Fritz Lang. “Dr. Mabuse, the Gambler”, movie, 1922.
Or even start to think about some kind of “wearables”, and then become a new type of fraud technological data psychic?

Fraud medium Colin Evans in levitation, 13 June 1938 (source Wikipedia).
We could even digg deeper into these “beliefs” and start looking at old illustrations and engravings that depicts relations to “things that we don’t understand”, that are “beyond our understanding”… and that possibly show “tools” or strange machinery to observe or communicate with these “unknown things” (while trying to understand them)?
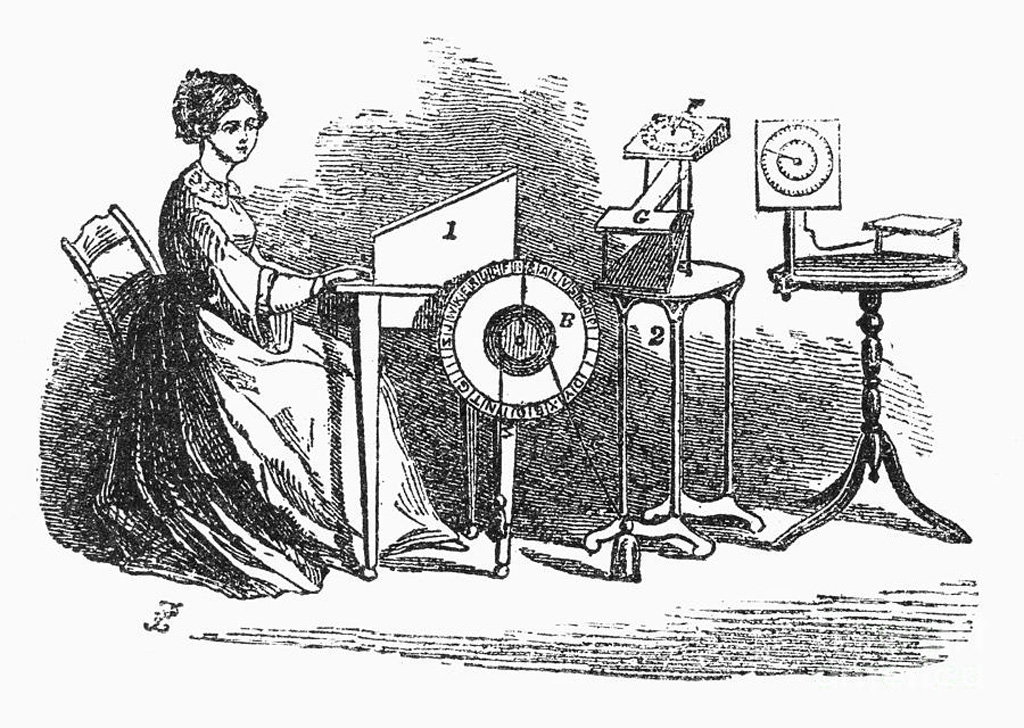
Spiritualism in 1855, author unknown.
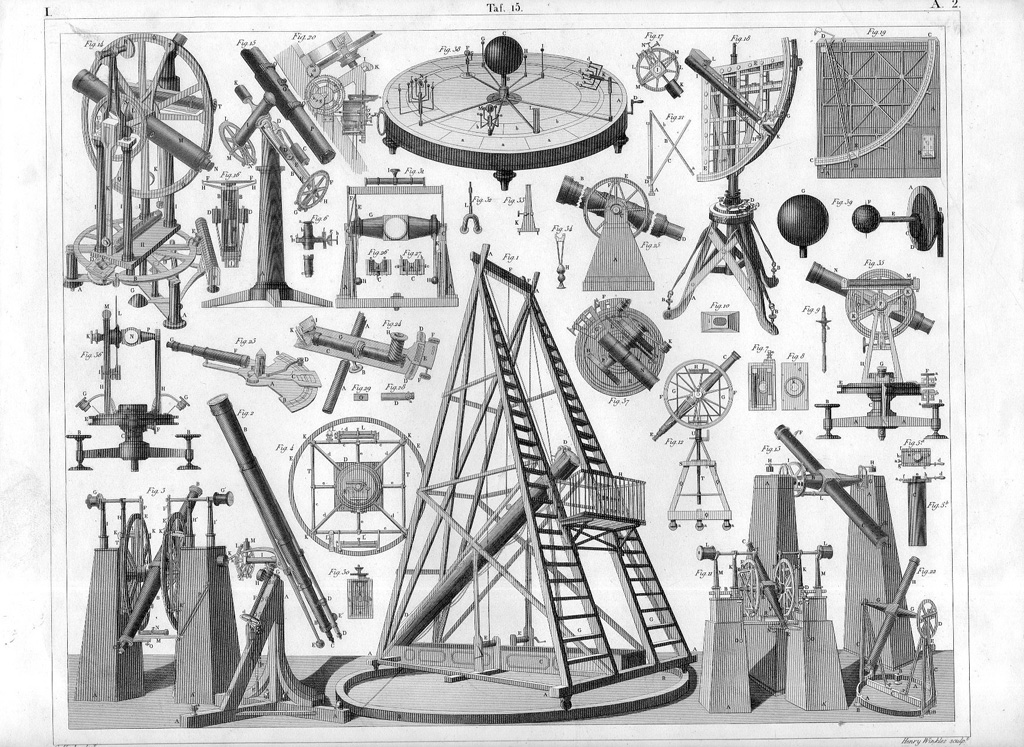
J.G. Heck. A plate from “The Iconographic Encyclopedia of Science, Literature and Art” published in 1851. Astronomy tools.
This last illustration could also drive us, by extension and a very straight shortcut , to the idea of the Sublime (in art, but also in philosophy), especially the romantic works of the painters from that period (late 18th and early 19th centuries, among them W. Turner, C. S. Friedrich, E. Delacroix, T. Cole, etc.) Submerged by the presentiment of a nature that was in all dimensions dominating humans, that remained at that time mostly unexplained and mysterious, if not dangerous and feared, some painters took on this feeling, named “sublime” after Edmund Burke’s Philosophical Enquiry (1757), and start painting dramatic scenes of humans facing the forces of nature.

Thomas Cole, “The Voyage of Life: Old Age”, 1842. National Gallery of Art, Washington DC.
It is not by chance of course that I’ll end my “esoteric comments about the brief” post with this idea of the Sublime. This is because recently, the concept found a new life in regard to technology and its central yet “unexplained, mysterious, if not dangerous and feared” role in our contemporary society. The term got completed at this occasion to become the “Technological Sublime”, thus implicitly comparing the once dominant and “beyond our understanding” Nature to our contemporary technology.
“American Technological Sublime” by D. E. Nye, published in 1994 (MIT Press) was certainly one of the first book to join the two terms. It continues the exploration of the social construction of technology initiated in his previous book, “Electrifying America” (MIT Press, 1990). More recently in 2011, the idea popup again on the blog of Next Nature in an article simply entitled The Technological Sublime.
So, to complete my post with a last question, is the Cloud, that everybody uses but nobody seems to understand, a technologically sublime artifact? Wouldn’ it be ironic that an infrastructure, which aim is to be absolutely rational and functional, ultimately contributes to creates a completely opposite feeling?
Quotes are from Dev Joshi’s brief, “The Everlasting Shadow“.